Early breach detection
with high-interaction deception
Deploy decoys in minutes. Detect intrusion earlier, reduce alert noise, and investigate suspicious access faster.
- High-interaction decoys across 30+ protocols
- Correlated attacker sessions with MITRE ATT&CK context
- Actionable alerts for faster triage
This is a simulated telemetry stream for design demonstration purposes.
Recognized by industry leaders
Momentum across leading cloud and security programs.
- Selected for the Cybersecurity AcceleratorAWS · CrowdStrike · NVIDIA
- Joined the NVIDIA Inception ProgramProgram member
Get started with NeroSwarm Honeypot
Deploy NeroSwarm to cut alert fatigue and gain real-time visibility into active intrusion attempts.
Intelligent Deception for Active Defense
Launch deception campaigns with pre-built templates to detect threats faster,
using hardware appliances or containerized decoys.

Emulate Key Protocols and Any Device with Deception
Our AI-powered honeypot platform emulates real protocols and real devices, from Windows and Linux hosts to services like SSH, RDP, LDAP, Redis, PostgreSQL, MongoDB, HTTPS, and more.
With instant alerting, your integrated channels notify you the moment a threat actor interacts with a decoy.
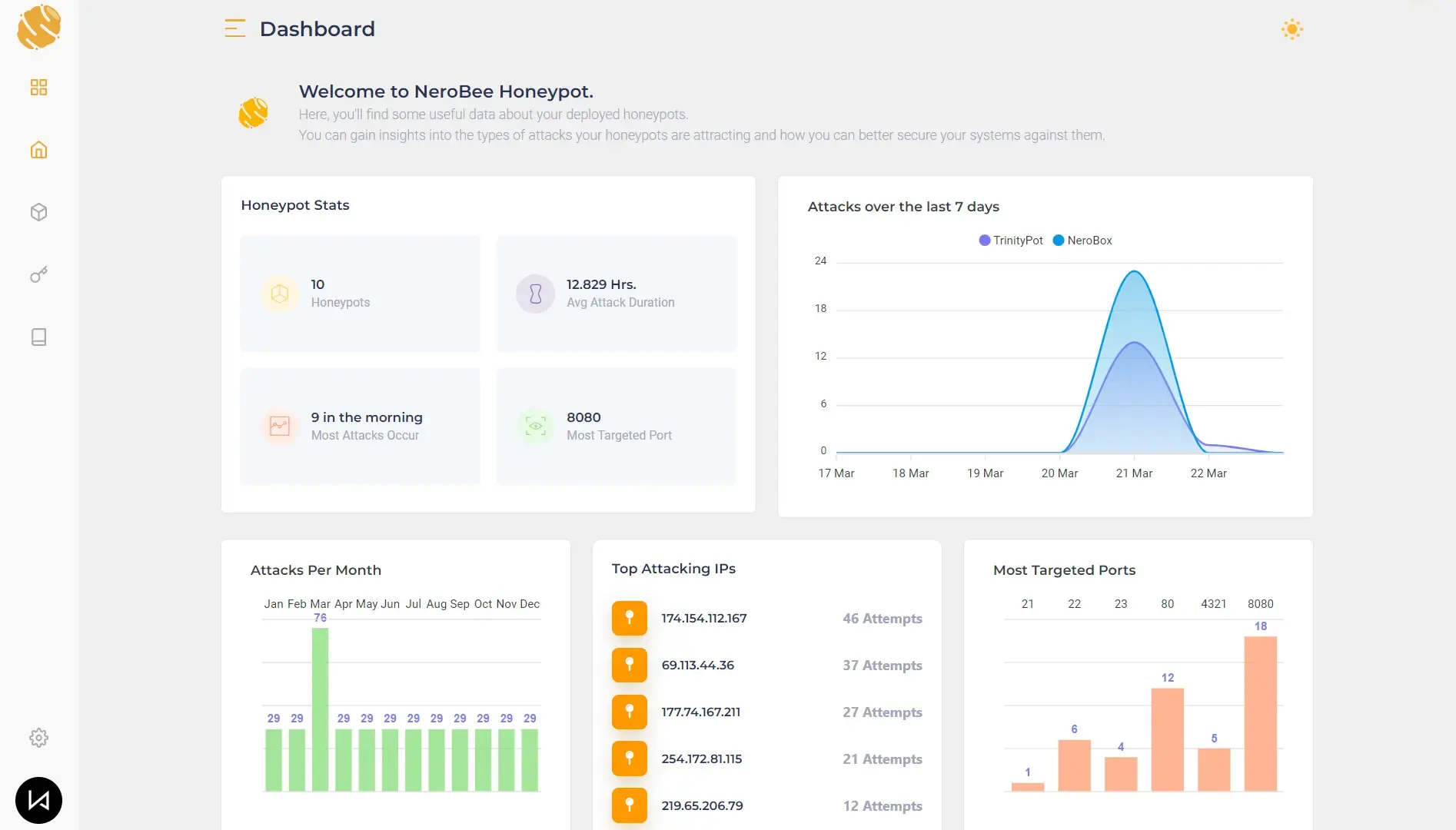
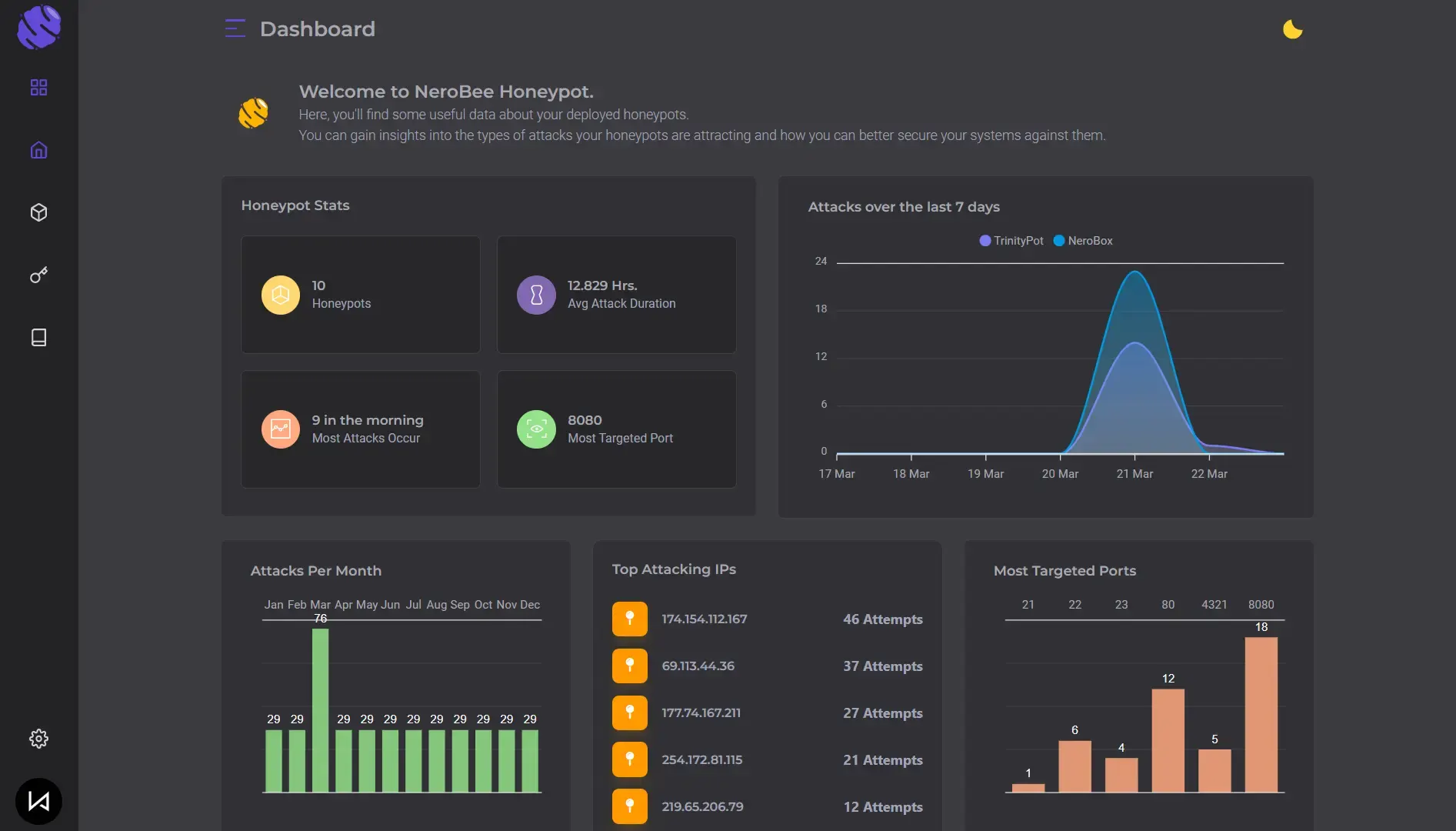
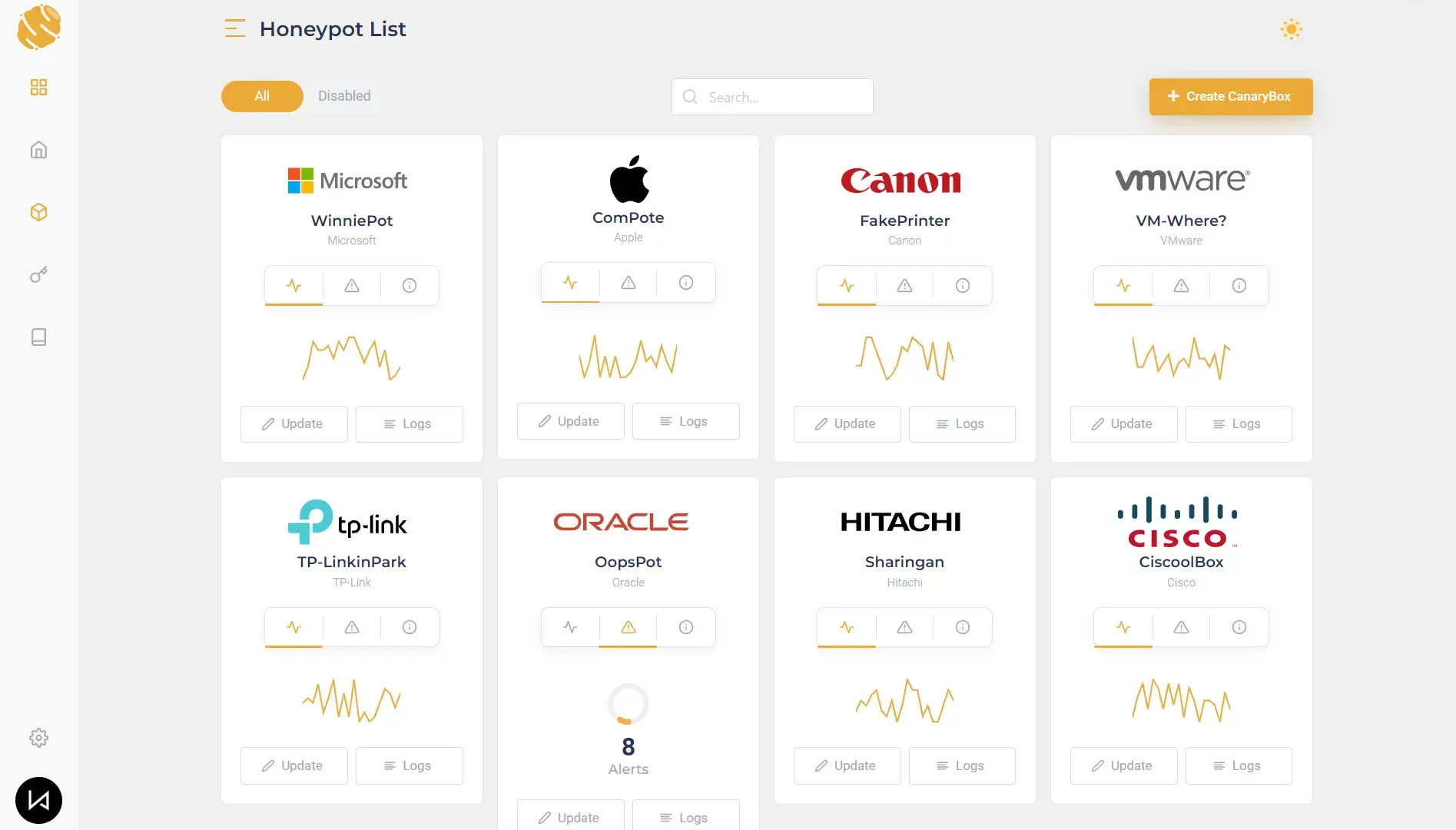
Comprehensive Dashboard and Insights
Our platform provides a clear dashboard with analytics to track activity across every deployed honeypot and surface high-signal attacker behavior.
Beyond detection, the data helps you map adversary techniques and spot repeatable patterns. We also integrate with common SIEMs via automated log shipping for seamless correlation.


Cyber Deception at Any Scale
Full visibility and stronger coverage at scale. An end-to-end platform in one place.
Early Intrusion Detection
Decoys detect attackers before real damage occurs, giving you time to respond with confidence.
Customizable Decoys
Create decoys that match your environment to attract targeted activity and expose attacker intent.
Operator-Friendly Dashboard
Easily manage your honeypots and view real-time threat activity through our intuitive dashboard.
Secure Networks with AI Honeypots
Our decoys use AI to mimic real systems, increasing detection depth while lowering operational risk.
Instant Notifications
Receive real-time notifications and alerts as soon as a threat actor engages with your honeypot.
CVE-Mapped Templates
Choose templates mapped to CVEs to emulate known exposures and lure realistic exploitation.
Layered Deception Defense
Deploy multiple decoys across your network to create layered coverage against intrusion and movement.
Realistic Services and Signals
Emulate real services and signals to attract authentic attacker behavior and strengthen detection fidelity.
High-signal alerts.
Every hit is a strong indicator of intrusion.
Get a live demo and see cyber deception in action within 45 minutes.
Unify Deception and Detection
Connect NeroSwarm to SIEM, XDR, and SOAR tools for advanced threat correlation.
Don't see the integration you need?
Deception Technology, Done Differently
We turns deception into an evidence pipeline that captures attacker intent, enriches context, and speeds up response.
Beyond bait and alert A deception first security model built for SOC operations.
Traditional deception often stops at an alert. NeroSwarm turns attacker interaction into strong telemetry you can trust with normalized fields, linked sessions, and output aligned with analyst triage.
- Signal over noise
- Every decoy hit is treated as a meaningful indicator, enriched into context your SIEM/XDR can correlate.
- Controlled interaction
- High interaction behavior is bounded by design and captures intent without exposing production assets.
- Operator ready output
- Telemetry is structured for investigation workflows with session linked events, consistent fields, and ATT&CK context.
Traditional deception
Often optimized for tripwires and alerting, but it leaves analysts with limited context.
- High alert volume with uneven confidence
- Weak session narrative across events
- Harder to operationalize in SOC workflows
- Alerts show presence but not behavior
- Analysts do not get a full attacker session story
NeroSwarm deception first
Designed to produce evidence quality telemetry with linked sessions, normalized fields, and strong correlation value.
- Every interaction carries strong confidence by nature
- Controlled engagement exposes attacker intent
- SOC ready output for SIEM/SOAR















